What is PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards formed in 2004 by Visa, MasterCard, Discover Financial Services, JCB International and American Express. Governed by the Payment Card Industry Security Standards Council (PCI SSC), the compliance scheme aims to secure credit and debit card transactions against data theft and fraud.
While the PCI SSC has no legal authority to compel compliance, it is a requirement for any business that processes credit or debit card transactions. PCI certification is also considered the best way to safeguard sensitive data and information, thereby helping businesses build long lasting and trusting relationships with their customers.
PCI MERCHANT LEVELS 1 – 4 AND COMPLIANCE REQUIREMENTS | SAQ, QSA | VISA | MASTERCARD
There are numerous Merchant Levels and varying compliance requirements for which merchants need to be aware of regarding PCI DSS. As for the technical definition of a merchant, it is “…any entity that accepts payment cards bearing the logos of any of the five members of the Payment Card Industry Security Standards Council (PCI SSC)…as payment for goods and/or services…”
Listed below are the Merchants levels, criteria, and related validation requirements for VISA and MasterCard. And though there are technically three (3) other major payment brands (AMEX, Discover, and JCB), compliance with the two (2) noted brands generally covers the others:
PCI DSS Compliance Levels
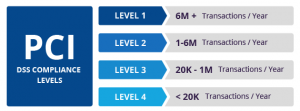
PCI compliance is divided into four levels, based on the annual number of credit or debit card transactions a business processes. The classification level determines what an enterprise needs to do to remain compliant.
Merchant Level: 1
• Merchant Criteria: (1). Any merchant, regardless of acceptance channel, processing more than 6,000,000 Visa transactions per year. (2). Any merchant that has had a data breach or attack that resulted in an account data compromise. (3). Any merchant identified by any card association as Level 1.
• Validation Requirements: (1). Annual Report on Compliance (“ROC”) by Qualified Security Assessor (“QSA”) – also commonly known as a Level 1 onsite assessment – or internal auditor if signed by officer of the company. (2). Quarterly network scan by Approved Scan Vendor (“ASV”). (3). Attestation of Compliance Form
Merchant Level: 2
• Merchant Criteria: 1 million – 6 million Visa or MasterCard transactions annually (all channels).
• Validation Requirements for VISA and MasterCard: (1). Annual Self-Assessment Questionnaire (“SAQ”). (2). Quarterly network scan by ASV. (3). Attestation of Compliance Form.
Merchant Level: 3
• Merchant Criteria: Merchants processing 20,000 to 1 million Visa or MasterCard e-commerce transactions annually
• Validation Requirements for VISA and MasterCard: (1). Annual Self-Assessment Questionnaire (“SAQ”). (2). Quarterly network scan by ASV. (3). Attestation of Compliance Form.
Merchant Level: 4
• Merchant Criteria: Less than 20,000 Visa or MasterCard e-commerce transactions annually, and all other merchants processing up to 1 million Visa or MasterCard transactions annually.
• Validation Requirements for VISA and MasterCard: (1). Annual Self-Assessment Questionnaire (“SAQ”). (2). Quarterly network scan by ASV. (3). Attestation of Compliance Form. Note: Ultimately, Compliance validation requirements set by acquirer.
PCI DSS Requirements
The PCI SSC has outlined 12 requirements for handling cardholder data and maintaining a secure network. Distributed between six broader goals, all are necessary for an enterprise to become compliant.
 Secure network
Secure network
- A firewall configuration must be installed and maintained
- System passwords must be original (not vendor-supplied)
Secure cardholder data
- Stored cardholder data must be protected
- Transmissions of cardholder data across public networks must be encrypted
Vulnerability management
- Anti-virus software must be used and regularly updated
- Secure systems and applications must be developed and maintained
Access control
- Cardholder data access must be restricted to a business need-to-know basis
- Every person with computer access must be assigned a unique ID
- Physical access to cardholder data must be restricted
Network monitoring and testing
- Access to cardholder data and network resources must be tracked and monitored
- Security systems and processes must be regularly tested
Information security
- A policy dealing with information security must be maintained
PCI DSS Certification
PCI certification ensures the security of card data at your business through a set of requirements established by the PCI SSC. These include a number of commonly known best practices, such as:
- Installation of firewalls
- Encryption of data transmissions
- Use of anti-virus software
In addition, businesses must restrict access to cardholder data and monitor access to network resources.
PCI-compliant security provides a valuable asset that informs customers that your business is safe to transact with. Conversely, the cost of noncompliance, both in monetary and reputational terms, should be enough to convince any business owner to take data security seriously.
A data breach that reveals sensitive customer information is likely to have severe repercussions on an enterprise. A breach may result in fines from payment card issuers, lawsuits, diminished sales and a severely damaged reputation.
After experiencing a breach, a business may have to cease accepting credit card transactions, or be forced to pay higher subsequent charges than the initial cost of security compliance. The investment in PCI security procedures goes a long way toward ensuring that other aspects of your commerce are safe from malicious online actors.
Here are some useful: PCI FAQ
About the PCI DSS
- What is PCI?
- Who has to comply?
- What is an Approved Scanning Vendor?
- What are the certification levels and what do they mean?
- Who needs to get external auditors for certification?
- What is the difference between a Qualified Security Assessor and an Approved Scanning Vendor?
Getting Certified with the PCI Compliance Service
- How does the PCI Compliance Service help me to get certified?
- What is the process to use the PCI Compliance Service for certification?
- How often do I need to scan?
- What IP addresses do I scan?
- How do I configure my IPS to allow the PCI scans?
- What about my Firewalls?
- Who needs to complete the self assessment questionnaire?
About the PCI Compliance Service
- How do I log into the PCI Compliance Service?
- How do I change my user login?
- Why do I get an “Invalid credentials” error?
- Why do I get an error stating “The subscription to which this user belongs is expired”?
- How do I reset my password?
- How do I start a questionnaire?
- How many IP addresses can I scan with my account?
- How do I purchase additional IP addresses to scan?
- How do I remove IP addresses from my account?
- How do I launch a PCI scan?
- Can I modify any of the scan settings?
- How do I view scan results?
- What PCI network reports are provided?
- What criteria causes a Passed or Failed compliance status in my PCI reports?
- Where can I view my overall PCI compliance status?
- What if I fail the PCI Compliance Service’s validation?
- What do I do if I pass the PCI Compliance Service’s validation?
- What report do I send to my acquiring banks?
- Can I submit reports directly to my acquiring banks?
- Does the PCI Compliance Service provide assistance with remediation?
- How can I get assistance understanding a vulnerability?
- What if my business has a vulnerability that it deems as an acceptable risk?
- What do I do if I think I have a false positive?
- Where do I find out more information about PCI?
- How do I contact support?
About the PCI DSS
What is PCI?
The Payment Card Industry (PCI) Data Security Standard details security requirements for members, merchants, and service providers that store, process or transmit cardholder data. To demonstrate compliance with the PCI Data Security Standard, merchants and service providers may be required to validate and conduct a network security scan on a regular basis as defined by the PCI Security Standards Council.
Network Security Scans are an indispensable tool to be used in conjunction with a vulnerability management program. Scans help identify vulnerabilities and misconfigurations of websites and IT infrastructure containing externally facing IP addresses. Scan results provide valuable information that supports efficient patch management and other security measures that improve protection against Internet hacking.
The current regulation PCI DSS v3.0 was released in October 2013 and applies to most merchants, banks and service providers on January 1, 2014. Companies compliant with previous PCI DSS v2.0 have an extended deadline and must comply by January 1, 2015.
Who has to comply?
Network Security Scan requirements apply to all merchants and service providers with external-facing IP addresses that collect, process or transmit payment account information. However, even if an entity does not offer web-based transactions, there are other services that make systems Internet accessible. Basic functions such as email and employee Internet access will result in the Internet-accessibility of a company’s network. These seemingly insignificant paths to and from the Internet can provide unprotected pathways into merchant and service provider systems and can potentially expose cardholder data if not properly controlled.
What is an Approved Scanning Vendor?
All PCI scans must be conducted by an approved scanning vendor, selected from the list of approved vendors athttps://www.pcisecuritystandards.org/. All compliant scanning vendors are required to conduct scans in accordance with a defined set of procedures. These procedures dictate that the normal operation of the customer environment is not to be impacted and that the vendor should never penetrate or alter the customer environment.
What are the certification levels and what do they mean?
Information about merchant levels and service provider levels can be found at https://www.pcisecuritystandards.org/.
Who needs to get external auditors for certification?
External auditors are required for annual audits of level 1 merchants and level 1 & 2 service providers. More information can be found at https://www.pcisecuritystandards.org/.
What is the difference between a Qualified Security Assessor and an Approved Scanning Vendor?
Qualified Security Assessors (QSA) are authorized to perform annual audits for merchants and service providers to document compliance with PCI. Approved Scanning Vendors (ASV) are authorized to perform the quarterly scans to show compliance with the PCI Data Security Standard. Several qualified security assessors incorporate approved scanning vendors into their solution. SureCloud is an Approved Scanning Vendor.
Getting Certified with the PCI Compliance Service
How does the PCI Compliance Service help me to get certified?
Our company is certified as a PCI Approved Scanning Vendor (ASV) to help merchants and their consultants validate and achieve compliance with the PCI Data Security Standard. The PCI Compliance Service is an on demand compliance testing and reporting service. Using the service, merchants can run PCI compliance scans, complete PCI self assessment questionnaires and submit compliance reports directly to acquiring banks. Our on demand delivery model makes the PCI Compliance Service available anytime from any browser, without software to install or maintain.
What is the process to use the PCI Compliance Service for certification?
Read “Getting Started with the PCI Compliance Service” to learn how to use the PCI Compliance Service for achieving compliance with the PCI Data Security Standard. The getting started guide is available for download fromhttp://www.qualys.com/enterprises/qualysguard/pci-compliance/.
How often do I need to scan?
A network security scan must be completed every 90 days by an approved PCI scanning vendor. Our company is a PCI approved scanning vendor (ASV). To achieve network status compliance using our PCI Compliance Service, all hosts must be scanned during the best practice scanning period and there can be no PCI vulnerabilities found from the scans during this period. The PCI Compliance Service defines the best practice scanning period to be 30 days prior to the current day. Using the Compliance Service, you can scan your network in segments and remediate/re-scan for vulnerabilities on target IPs. Segmented scanning allows you to scan hosts that you have remediated without having to scan your entire network.
What IP addresses do I scan?
All external IP addresses must be scanned for PCI compliance.
The document PCI DSS Security Scanning Procedures describes in detail the scope of PCI security scanning required for PCI compliance. The latest version of this document can be found at the PCI Security Standards Council’s website:https://www.pcisecuritystandards.org/pdfs/pci_scanning_procedures_v1-1.pdf
In this document, the section called “Scope of PCI Security Scanning” starting on page 1 states the following:
“The PCI requires all Internet-facing IP addresses to be scanned for vulnerabilities. If active IP addresses are found that were not originally provided by the customer, the ASV must consult with the customer to determine if these IP addresses should be in scope. In some instances, companies may have a large number of IP addresses available while only using a small number for card acceptance or processing. In these cases, scan vendors can help merchants and service providers define the appropriate scope of the scan required to comply with the PCI. In general, the following segmentation methods can be used to reduce the scope of the PCI Security Scan.
- Providing physical segmentation between the segment handling cardholder data and other segments
- Employing appropriate logical segmentation where traffic is prohibited between the segment or network handling cardholder data and other networks or segments
Merchants and service providers have the ultimate responsibility for defining the scope of their PCI Security Scan, though they may seek expertise from ASVs for help. If an account data compromise occurs via an IP address or component not included in the scan, the merchant or service provider is responsible.”
How do I configure my IPS to allow the PCI scans?
As per the requirements in the PCI scanning procedure specifications, an IPS must be set to not block a scan. The service provides multiple scanners for external (perimeter) scanning, located at the Security Operations Center (SOC) that is hosting the PCI Compliance Service. The scanner IP addresses are 64.39.96.0/20 (64.39.96.1-64.39.111.254). Depending on your network, it may be necessary to add the scanner IPs to your list of trusted IPs, so the service can send probes to the IP addresses in your account during scan processing.
The document PCI DSS Security Scanning Procedures describes in detail the scanning procedures required for PCI compliance. The latest version of this document can be found at the PCI Security Standards Council’s website:https://www.pcisecuritystandards.org/pdfs/pci_scanning_procedures_v1-1.pdf
Your network protection systems should be configured to not interfere with the vulnerability scanning, as described in the document referenced above. In this regard, the section “Scanning Procedures” item 13 states the following:
“Arrangements must be made to configure the intrusion detection system/intrusion prevention system (IDS/IPS) to accept the originating IP address of the ASV. If this is not possible, the scan should be originated in a location that prevents IDS/IPS interference”
Security scanning procedures are outlined as part of the PCI Data Security Standard. Supporting documents published by the PCI Security Standards Council can be found at:
https://www.pcisecuritystandards.org/tech/supporting_documents.htm
What about my Firewalls?
Firewall configurations do not need to be changed.
Who needs to complete the self assessment questionnaire?
All merchants at level 2, 3 and 4 and all service providers at level 3 must complete a PCI self assessment questionnaire (SAQ) on an annual basis. Level 4 merchants should contact their acquiring banks for requirements. Note: In Canada, for Visa, merchants must have their SAQ validated by a PCI qualified security assessor (QSA) prior to submitting the SAQ to acquiring banks.
About the PCI Compliance Service
How do I log into the PCI Compliance Service?
When your PCI Merchant account is created, you will receive a registration email. In the body of this email you will find the URL to the PCI Merchant application and a secure link to your account credentials. With your login and password, log into the service at the URL provided and you will be directed to your Home page.
How do I change my user login?
At account creation time, you are assigned a user login for the PCI Merchant application. You can change your user login at any time. To do so, select Account->Users on the left menu. Identify your own user account (it will be in bold) and click Edit. Then select the “Change User Login” link. Enter your current login in the field provided and then a new login in the “New User Login” field. Note that your user login must be unique to the PCI Merchant application, and must include the @ character, such as john@qualys. After saving your new user login, log back into the service.
Why do I get an “Invalid credentials” error?
When logging into the PCI Compliance Service, the user login and password entered did not match the information we have stored at our Security Operations Center (SOC). Please check to make sure the information you entered is correct. Note that user logins and passwords are case sensitive so make sure Caps Lock is turned off.
If you do not know your password, the service provides methods for requesting a new password. You can click the “Forgot Password” link on the Login page to have a new password automatically generated. After providing your user login, you will receive an email with a link to your new credentials. Alternatively, you can contact another user in your account and request that they reset your password through the PCI Compliance application. To reset another user’s password, go to the Users list (Account->Users) and select Edit to edit the account for the user who is requesting a new password. On the Edit User page, select the “Reset Password” link. A new password is automatically generated for the user’s account and an email with login instructions is sent to the user.
If you do not know your user login, contact another user in your account and request that they look it up for you. To do this, the other user can go to the Users list (Account->Users) and select Edit to edit your account. On the Edit User page, your username is displayed.
If you need additional help, email Customer Support at:
Why do I get an error stating “The subscription to which this user belongs is expired”?
When logging into the PCI Compliance Service, the user login and password you entered is for a user that belongs to a subscription which is expired. If your subscription has multiple users and you are not the primary contact for the subscription, we recommend that you first consult the primary contact. The primary contact user appears in bold on the Users list (Account->Users). If you would like to activate your subscription, please contact your sales representative or Customer Support. You can email Customer Support at
How do I reset my password?
At account creation time, the PCI Compliance Service provides a randomly generated “strong” password for your account. You can change your password at any time. To do so, select Account->Users from the left menu. Identify your own user account (it will be in bold) and click Edit. Then select the “Change Password” link. Enter your current password in the field provided and then a new password in the “New Password” field. Your password must be a minimum of 6 characters and must include a mixture of alpha and numeric characters. After saving your new password, log back into the service.
How do I start a questionnaire?
The PCI self assessment questionnaire is available online through the PCI Compliance Service’s web application. To start a new questionnaire, select Questionnaires->New Questionnaire from the left menu.
How many IP addresses can I scan with my account?
AAll IP addresses in your account may be scanned. To view the IPs in your account, go to Account->IP Assets. You may add IPs up to the limit defined for your account. The maximum number of IPs allowed in your account can be viewed by selecting Account->Settings on the left menu, and then scrolling down to the Subscription Information section.
How do I purchase additional IP addresses to scan?
To purchase additional IP addresses to scan, please contact your sales representative.
How do I remove IP addresses from my account?
This is an simple self service task as Qualys no longer requires IP Removals in PCI to go through support. Users can do it themselves by going to Account > IP Assets and click ‘Remove IP’. If you have issues, then contact customer support.
How do I launch a PCI scan?
To launch a PCI scan, log into the PCI Compliance Service and select Network->New Scan from the left menu. (Or click Start a Scan on the Home page.) Next supply a title for the scan in the Title field and select a bandwidth level from the Bandwidth menu. It’s recommended that you keep the default bandwidth level of Medium. Identify the IPs you want to scan in the Target IPs section. The All IPs option is selected by default, meaning that all IPs in your account will be scanned. You may choose the Select IPs option to scan a limited number of IPs. After specifying your scan target, click “OK” to start the scan.
Optionally, you can schedule the scan to start at a later time. To do so, select the Schedule for Later option and then specify the start date (month, day and year) and start time (hours and minutes). Also select your local time zone. You may enter any date/time within the next 90 days.
Can I modify any of the scan settings?
Underlying scan settings have been optimized to test compliance with the PCI Data Security Standard. There is one user-configurable scan performance setting — Bandwidth Level — which affects overall scan performance. Several bandwidth levels are provided, and each level represents multiple settings. It’s recommended that you keep the default bandwidth level Medium to get started. You can select another level when you launch or schedule a scan. See the online help for descriptions of the various bandwidth levels and their settings.
How do I view scan results?
The Scans page lists all running and completed scans. To see this page, select Network->Scan Results from the left menu. From this list, you can search and view scan tasks, view detected vulnerabilities that must be fixed to achieve PCI compliance, and download the scan results. In the Scan Results report, the Detailed Results section shows all vulnerabilities detected by the service (not limited to vulnerabilities that must be fixed to achieve PCI compliance).
What PCI network reports are provided?
The service provides two PCI network reports — PCI Executive Report and PCI Technical Report. The PCI reports provide similar information suitable for different workflows. The PCI Executive Report is used to submit to the acquiring bank to document PCI compliance. This report provides summary level information only. The PCI Technical Report is used to identify vulnerabilities and prioritize remediation. For this reason, the PCI Technical Report includes technical details to assist with remediation. To create the PCI network reports, select Network->Compliance Status from the left menu and then click “Generate”.
What criteria causes a Passed or Failed compliance status in my PCI reports?
The PCI Compliance Service produces reports that include an overall PCI compliance status of Passed or Failed. An overall PCI compliance status of Passed indicates that all hosts in the report passed the PCI DSS compliance standards set by the PCI Council. A host compliance status is provided for each host. A PCI compliance status of Passed for a single host/IP indicates that no vulnerabilities or potential vulnerabilities, as defined by the PCI DSS compliance standards set by the PCI Council, were detected on the host. The criteria used to calculate a passed or failed compliance status can be found athttp://www.qualys.com/enterprises/qualysguard/pci-compliance/pass-fail-criteria/
Where can I view my overall PCI compliance status?
You can view the current PCI compliance status for your network and its hosts on the Compliance Status page by selecting Network->Compliance Status. The Compliance Status chart at the top of the page displays the current compliance status of your entire network, including all hosts. The Host Status list at the bottom of the page displays the current compliance status for hosts in your account.
What if I fail the PCI Compliance Service’s validation?
You can view a list of detected vulnerabilities and potential vulnerabilities by selecting Network->Vulnerabilities on the left menu. All detected vulnerabilities are listed, including vulnerabilities that must be fixed to pass PCI compliance as well as vulnerabilities that we recommend that you fix. For each vulnerability you can view detailed information for remediation so that you can quickly fix and eliminate the vulnerability.
After remediation, run another PCI scan and check your overall compliance status. Repeat these steps until the overall PCI compliance status is “Compliant”.
What do I do if I pass the PCI Compliance Service’s validation?
You can check your overall compliance status on the Compliance Status page by selecting Network->Compliance Status. If your overall PCI compliance status is “Compliant”, then you are ready to generate, save and submit network reports. To do so, click the “Generate” icon and provide report information to be submitted to your acquiring banks. Then click the “Generate” button to generate PCI network reports. Review the reports and click “Save & Submit” to save the reports in your account and submit the PCI Executive Report electronically to banks in your account.
For other banks without electronic submission enabled, you need to download and print the PCI Executive Report and then send it manually via mail. Saved network reports appear on the Submitted Reports list in your account.
What report do I send to my acquiring banks?
The PCI Executive Report is appropriate for submission to your acquiring banks. To meet PCI compliance, the PCI Executive Report must indicate an overall PCI compliance status of Passed. This status is reported only when the required vulnerabilities are fixed and validated by a PCI scan.
Can I submit reports directly to my acquiring banks?
Banks are able to sign up to use the PCI Compliance Service, enabling them to view submitted PCI compliance documents and track PCI compliance status for their merchants through the PCI Compliance Service’s web application.
If your acquiring bank is signed up with the PCI Compliance Service and it is defined for your account, then you can submit questionnaires and scan reports directly to the bank.
To see a list of participating banks, select Account->Settings from the left menu and then scroll down to the Bank Information section. Click Edit and look at the banks listed in the Bank Name menu. These are participating banks.
If your bank is not a participating bank, then it will not appear in the Bank Name menu. Scroll down to the Other Banks section at the bottom of the page and enter the bank name in the field provided. If you don’t have a participating bank, then no bank has direct access to your submitted documents through the PCI Compliance Service’s web application. You must download submitted documents in PDF format and send them to your acquiring bank using a method outside of the application.
Does the PCI Compliance Service provide assistance with remediation?
Yes. The PCI Compliance Service provides links to fixes or workarounds from the PCI Technical Report and from the current vulnerabilities list to help network administrators remedy vulnerabilities. Our Security Engineers have validated all solutions in our vulnerability lab to ensure they function as specified.
How can I get assistance understanding a vulnerability?
Please contact Customer Support for assistance with understanding a vulnerability. To do this, simply log into the PCI Compliance Service, and select Contact Support from the left menu. On the page provided you may send an email to Customer Support with your questions.
What if my business has a vulnerability that it deems as an acceptable risk?
In order to be compliant with the PCI requirements, all vulnerabilities and potential vulnerabilities, as defined by the PCI DSS compliance standards set by the PCI Council, must be remediated. If you have a Failing Report due to an acceptable risk, then you can submit your report to your acquirer and request a temporary exception from them, until the issue can be fully remediated, as is required per the PCI Standards for all failing vulnerabilities.
What do I do if I think I have a false positive?
It’s possible after fixing all PCI vulnerabilities and potential vulnerabilities that you have an issue that doesn’t seem to apply to the host. In this circumstance, you may request an exception that will be considered by us as a false positive.
Before making this request, complete all remediation steps to fix vulnerabilities by following these guidelines:
- Work with your system administrator to fix all vulnerabilities in your scan results using the recommended solutions. A custom solution is provided for each vulnerability in the vulnerability details.
- Re-scan after fixing vulnerabilities to validate that systems are not vulnerable. You can re-scan as often as necessary to track remediation progress.
- Be sure to fix all vulnerabilities except the false positive issues. Your last re-scan should show only the false positive issues.
If you followed the guidelines above and believe that the PCI Compliance Service has identified a false positive in your scan, then use the steps below to submit a false positive request to Technical Support.
- Select Network->Vulnerabilities from the left menu. The Current Vulnerabilities list displays all current vulnerabilities that were detected on hosts from the most recent scans. You can use the search options in the Vulnerability Report Settings section to search for vulnerabilities.
- Select the check box to the left of each vulnerability you want to include in your request and click the Review False Positives button. Note it’s not possible to select a check box for a vulnerability that is not required to fix to pass PCI compliance.
- On the Request False Positives page, provide a detailed explanation for each selected vulnerability as to why you believe it is a false positive. Your explanation should include steps taken to validate that it is a false positive. You have the option to enter one reason for multiple false positives. To do this, select the check box “Use same comment for all the following requests”.
- Click the Submit False Positive Request button. Note that an error will occur if you select a vulnerability without providing an explanation.
An email is sent to Technical Support for review. A Technical Support representative will work with you to determine if the identified issue is a false positive and will send an email response confirming the decision.
- If the false positive request is approved, then the vulnerability will no longer show up in scan results for the specific host.
- If the false positive request is not approved, then you must fix the vulnerability in order to pass PCI compliance standards.
Where do I find out more information about PCI?
More information about PCI can be found at the following sites:
- https://www.pcisecuritystandards.org/
- https://www.mastercard.com/us/company/en/whatwedo/site_data_protection.html
- http://www.mastercardsecurity.com
- http://www.visa.com/cisp
- http://www209.americanexpress.com
- http://partner.jcbcard.com/security/jcbprogram/
- https://www.discovernetwork.com/merchants/data-security/disc.html
How do I contact support?
Customers can contact customer support at any time. Simply log into the PCI Compliance Service, and select Contact Support from the left menu. On the page provided you may submit an email directly to your PCI Compliance Service provide

