FastNetMon – A high performance DoS/DDoS load analyser built on top of multiple packet capture engines (NetFlow, IPFIX, sFLOW, SnabbSwitch, netmap, PF_RING, PCAP). What can we do? We can detect hosts in our networks sending or receiving large volumes of packets/bytes/flows per second. We can call an external script to notify you, switch off a server, or blackhole the client. To enable sFLOW, simply specify IP of the server running FastNetMon and specify (configurable) port 6343 To enable netflow, simply specify IP of the server running FastNetMon and specify (configurable) port 2055. What is a “flow” in FastNetMon terms? It’s one or multiple UDP, TCP, or ICMP connections with unique src IP, dst IP, src port, dst port, and protocol.
 Features:
Features:
- Complete BGP Flow Spec support, RFC 5575
- Process and distinguish incoming and/or outgoing traffic
- Trigger block/notify script if an IP exceeds defined thresholds for packets/bytes/flows per second
- Thresholds can be configured per-subnet with the hostgroups feature
- Announce blocked IPs via BGP to routers with ExaBGP
- GoBGP integration for unicast IPv4 announcements (you need build support manually).
- Full integration with Graphite and InfluxDB
- API (you need build support manually)
- Redis integration
- MongoDB integration
- Deep packet inspection for attack traffic
- netmap support (open source; wire speed processing; only Intel hardware NICs or any hypervisor VM type)
- SnabbSwitch support (open source, very flexible, LUA driven, very-very-very fast)
- Filter NetFlow v5 flows or sFLOW packets with LUA scripts (useful for excluding particular ports)
- Supports L2TP decapsulation, VLAN untagging and MPLS processing in mirror mode
- Works on server/soft-router
- Detects DoS/DDoS in as little as 1-2 seconds
- Tested up to 10Gb with 12 Mpps on Intel i7 3820 with Intel NIC 82599
- Complete plugin support
- Captures attack fingerprints in PCAP format
- Complete support for most popular attack types
Supported platforms
- Linux (Debian 6/7/8, CentOS 6/7, Ubuntu 12+)
- FreeBSD 9, 10, 11
- Mac OS X Yosemite
Supported architectures
- x86 64 bit (recommended)
- x86 32 bit
Distributions Supported
- Part of CloudRouter distribution
- Part of official FreeBSD ports, manual install
- Amazon AMI image
- VyOS based iso image with bundled FastNetMon
- Docker image
- Binary rpm packages for CentOS 6/7 and Fedora 21
- Automatic install script forDebian/Ubuntu/CentOS/Fedora/Gentoo
- Automatic install script for Mac OS X
- Manual install on Slackware
- Manual install for VyOS
Supported packet capture engines
- NetFlow v5, v9
- IPFIX
v4 (dev branch only), v5
- Port mirror/SPAN capture with PF_RING (with ZC/DNA mode support need license), SnabbSwitch, NETMAP and PCAP

| Name | Capture speed | Installation | CPU load | Platforms | Cost | Accuracy of attack detection | Speed of attack detection |
|---|---|---|---|---|---|---|---|
| netmap | Up to wire speed (10GE, 14 MPPS) | Need kernel module and NIC driver patch ixgbe provided. For FreeBSD could need kernel rebuild but patches are included to kernel | Normal | Linux, FreeBSD | BSD | Very accurate | Very fast |
| PF_RING | Up to 2-3 MPPS, 2-3 GE | Need kernel module install | Very big | Linux only | GPLv2 | Enough accurate | Very fast |
| PF_RING ZC | Up to wire speed (10GE, 14 MPPS) | Need kernel module + patched drivers (provided in package) | Normal | Linux only | Commercial ~200 euro | Very accurate | Very fast |
| pcap | very slow, 10-100 mbps | Simple | huge | FreeBSD, Linux | GPL | Not so accurate | Very fast |
| sFLOW | Up to 40-100GE | Very simple | Small | Linux, FreeBSD, MacOS | Free | Accurate but depends on sampling rate (1-128 sampling rate recommended but significantly depends on traffic in network) | Very fast |
| NetFlow | Up to 40-100GE | Very simple | Small for FastNetMon but could be huge for network equpment if implemented in software way | Linux, FreeBSD, MacOS | Free but could require additional licenses or hardware from network equipment vendor | Not so accurate | So slow, up to multiple minutes depends on flow timeout configuration on routers |
| AF_PACKET | Up to 2 MPPS/5-10GE | Very simple | Normal-huge | Linux (since 3.6 kernel) | GPLv2 | Very accurate | Very fast |
Install
For Debian 6, 7, 8 and CentOS 6, 7 and Ubuntu 14.04 and Fedora and Gentoo you should use the automatic installer:
wget https://raw.githubusercontent.com/pavel-odintsov/fastnetmon/master/src/fastnetmon_install.pl -Ofastnetmon_install.pl sudo perl fastnetmon_install.pl
Please keep in mind! We track some information about your machine (os type and distro version). If you do not want to share this information, please add flag
--do-not-track-me
To intstall script call. But in this case we can’t improve FastNetMon for your distribution.
It’s REQUIRED to add all of your networks in CIDR notation (11.22.33.0/24) to the file /etc/networks_list in the form of one prefix per line. If you are running this software on an OpenVZ node, you may not need to specify networks explicitly, as we can read them from /proc/vz/veip.
You can whitelist prefixes by adding them to /etc/networks_whitelist (CIDR notation too).
Start main process:
/opt/fastnetmon/fastnetmon
Start the client process in another console:
/opt/fastnetmon/fastnetmon_client
To enable fastnetmon to start on server startup, please add the following line to /etc/rc.local:
/opt/fastnetmon/fastnetmon --daemonize
If something goes wrong, please check logs:
tail -f /var/log/fastnetmon.log
When an incoming or outgoing attack occurs, the program calls a bash script twice (if it exists):
/usr/local/bin/notify_about_attack.sh
The first time when threshold exceed (at this step we know IP, direction and power of attack). Second when we collect 100 packets for detailed audit of what happened.
A sample script is provided and can be installed as follows:
wget https://raw.githubusercontent.com/pavel-odintsov/fastnetmon/master/src/notify_about_attack.sh -O/usr/local/bin/notify_about_attack.sh chmod 755 /usr/local/bin/notify_about_attack.sh
After downloading the file, you need to open it and configure the ’email_notify’ option as required.
You can use an alternative python script from here.
If you want to use unstable development branch, please use this syntax:
wget https://raw.githubusercontent.com/pavel-odintsov/fastnetmon/master/src/fastnetmon_install.pl -Ofastnetmon_install.pl sudo perl fastnetmon_install.pl --use-git-master
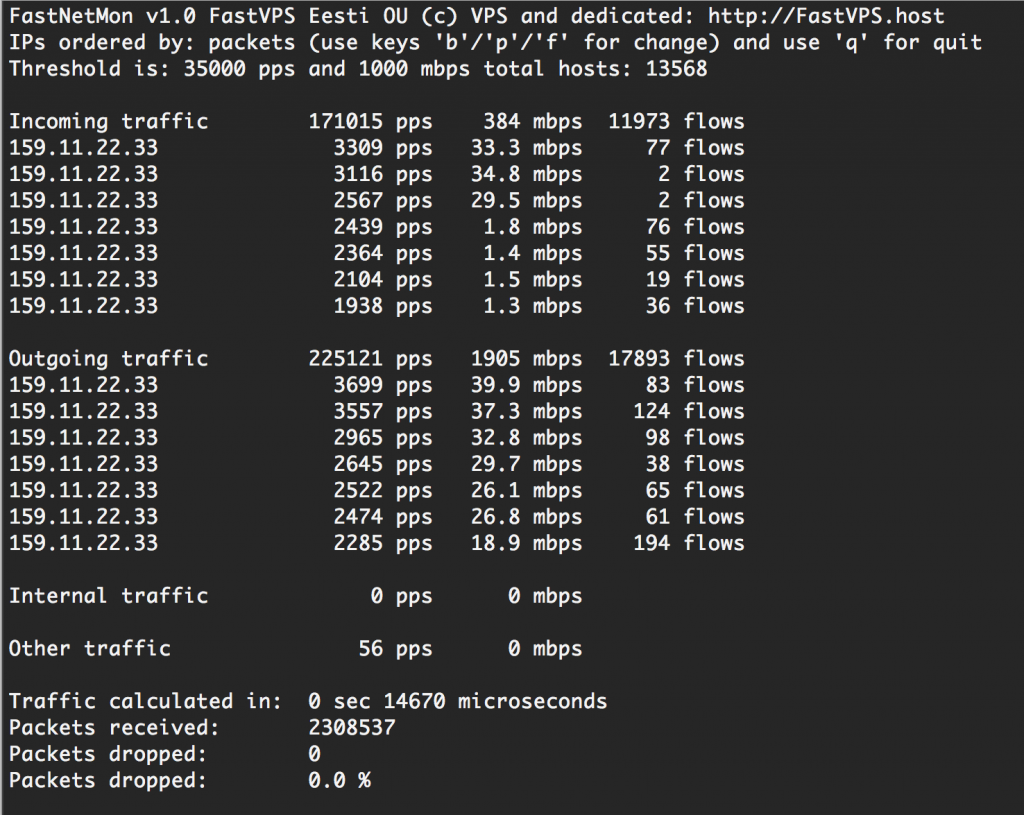
Example deployment scheme: