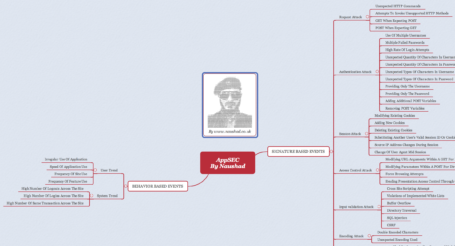
Here is my personally built and tested collection of incident response playbook reference guide – first aid tips and preparation guidance to limit damage and protect your mission. A critical principle of medicine applies equally well to cybersecurity incident responses – Do No Harm. Organisations face many pitfalls that can dramatically increase the negative impact of an incident. These guides are designed to help CSIRT (Computer Security Incident Response Team) manage a cybersecurity incident while avoiding common errors, increasing both the effectiveness and efficiency of your incident response efforts.
Threat Intelligence Report
Threat Intelligence: Staying Ahead Of Cyber Criminals, The threat intelligence likewise is an analysis of information collected about the cyber threat so that it provides reliable and structured information about cybersecurity threats. ReadMore
Hacker Business Models
An Inside Look at Business Models of Hackers, The industrialized hackers are intent on one goal–making money. They also know the basic rules of the business of increasing revenues while cutting costs.
Phishing Incident Response
The playbooks define the procedures for security event investigation and response, a written guidance for identifying, containing, eradicating and recovering from cybersecurity incidents. Full file via SlideShare
Defend DDoS Attacks
DDoS attacks are making the headlines but if you architect your infrastructure right at the DNS layer, you can significantly reduce the impact. ReadMore
IT Guys Life in Hell
Pentesting: Exploiting: how the system reacts to an attack, which weak spots exist that could be breached if any, and what data could be stolen from an active system.
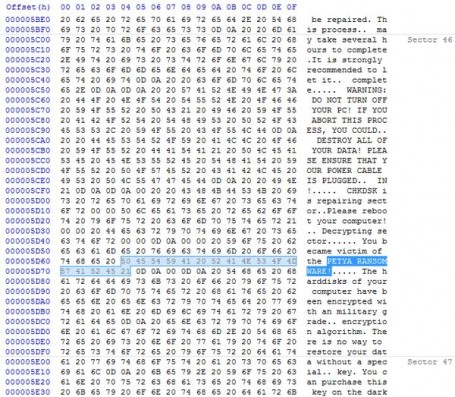
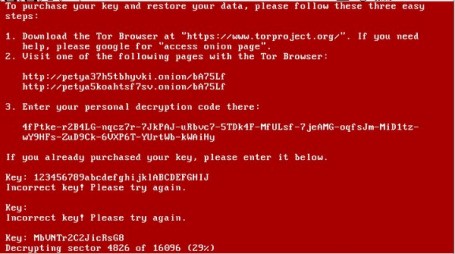
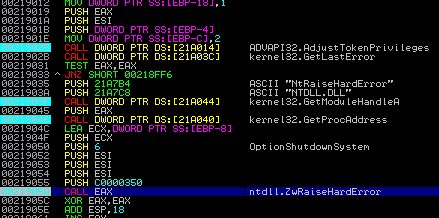
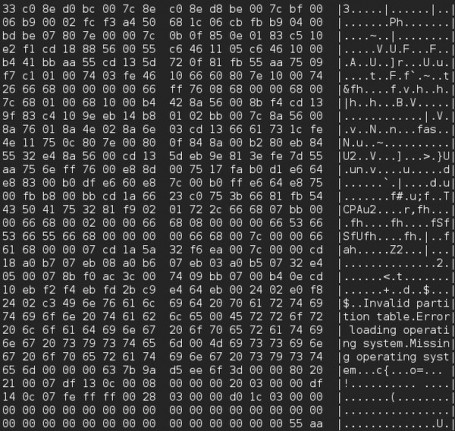
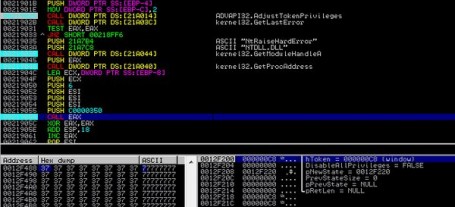
NotPetya Ransomware Outbreak
As I expected, On June 27, several organizations in Europe reported ransomware infecting their systems,!. The Wisdom of Crowds Intelligence Full Report -it’s not over yet!
Crowd Sourced Intelligence Doc
WannaCry stopped? No, this is just the beginning. Warm up! Expect more!. Full Report All say that the threat is stopped, but this is untrue. «Kill Switch» only slowed its progress.
MobileSEC Testing Guide
The Mobile Security Testing Guide (MSTG) is a comprehensive manual for mobile app security testing and reverse engineering PlayBook
High Performance DoS Analyzer
DOS/DDoS Load Analyser built on top of multiple packet capture engines (NetFlow, IPFIX, sFLOW, SnabbSwitch, Netmap, PF_RING, PCAP). Detect networks sending/receiving large volumes of packets
Penetration Testing Framework
A penetration tester’s job is to demonstrate and document a flaw in security. In a normal situation, a pen tester will perform reconnaissance to find some vulnerabilities
SSH Server Auditing: ssh-audit
SSH Audit is a tool for ssh server auditing. Features: Banner grab, Detect SSH1 protocol and zlib compression; * gather key-exchange, encryption & message authentication etc..
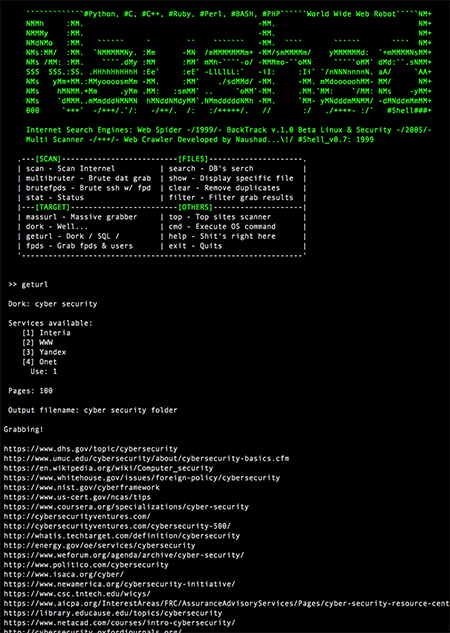
Search Machine Since: 1999
My Own Search Engine (Crawler / Spider) 1st developed in 1999 for the Data mining, Text search, Large document collections, Media Monitoring, Text analytics & Document Analysis
USB Anti Forensic Tool: USBdeath
Anti-forensic tool that writes udev rules for known usb devices and do some things at unknown usb device insertion or specific usb device removal.
Information Sensitivity Policy
The Information Sensitivity Policy is intended to help employees in determining appropriate technical security measures which are available for electronic
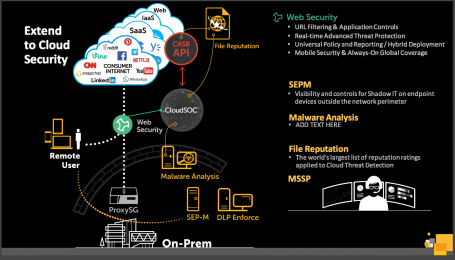
Secure Unified Communication
Unified communications infrastructure threats and defense strategies and cost savings for businesses. White paper written by Naushad and Gabriela
Securing VoIP
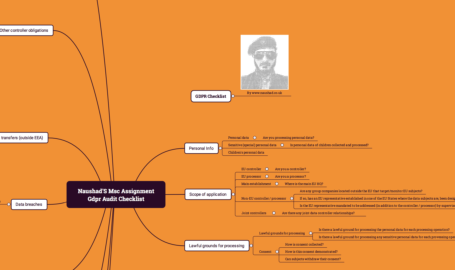
In this White paper I outlined different approaches to VoIP security and best practices to ensure infrastructure security is intact for making VoIP security a reality by Naushad MSc – Assignment
Modern Disaster Recovery Tools
No More Excuses -I’m Building my own a Modern Disaster Recovery toolkit, How to monitor your strategy to alert you to moves, adds, and changes that may break your plan
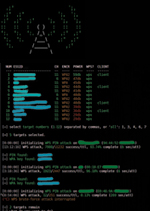
Avoid the WPA Wireless Attack
The latest crack in wireless security, specifically, the Wi-Fi Protected Access (WPA) security standard, can threaten the safety of enterprise networks and company information or data
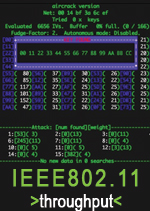
Security on Throughput of IEEEE
Effect of Security on Throughput of IEEE802.11b/g Protocols. Opportunistic Encryption (O-E): In this paper, I propose a framework called O-E that uses an acceptable signal to noise ratio.
GDPR will require 28,000 DPOs
European Union data protection rules will require the appointment of 28,000 data protection officers (DPOs) in the next two years in Europe alone, according to a study.
9 Important Fact:Colocation
With applications supporting your key customer interactions and business functions, all aspects of your IT infrastructure must be scrutinised – including your colocation provider.
NMAP DeepDive
Nmap is a great tool for discovering the network services and ports that your server is exposing to the network. In this guide, I will show you some of the hidden features of the NMAP
CCISO Table of Contents
EC-Council’s CCISO Program has certified leading information security professionals around the world. A core group of high-level information security executives
Blocking Tor proxy [business]
Blocking Tor proxy users to your Linux server, One of the main reasons is improved security, Here we show a way to make the server appear offline only for Tor users (by sending a TCP RST packet to close the connection). ReadMore
Top 100 Hacking Books
This list for everyone who is interested in ethical hacking, beginners or professionals both. These top 100 hacking books pdf list is created based on the public reviews given for the books.
Cyberthreat Defence Report
An organization’s own staff is its biggest cyber security weakness, a new survey from CyberEdge Group claims.

























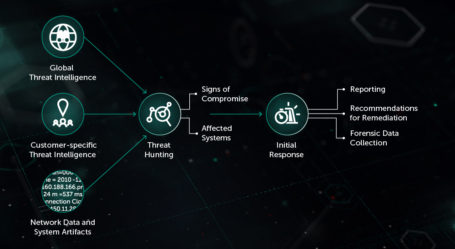
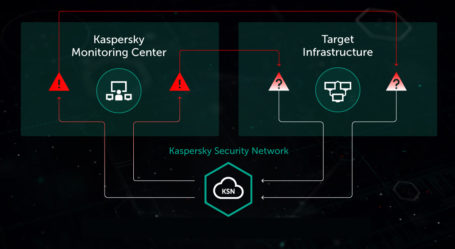
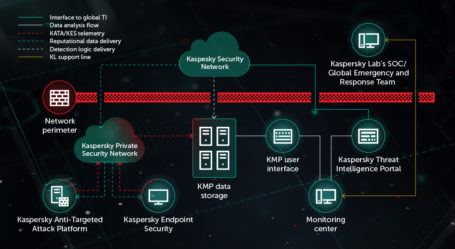
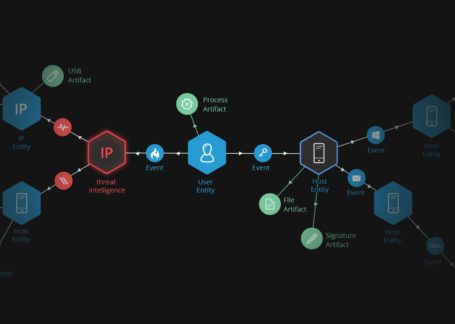


 Special Ops Project: Threat intelligence researchers hunting various potential spyware, adware, trojans, keyloggers, bots, worms, and hijackers, in real time. The CyberSecurity landscape has changed. No longer are we protecting against a piece of malicious code – we are defending against persistent adversaries. Find out more about APT’s or Advanced Persistent Threats. (
Special Ops Project: Threat intelligence researchers hunting various potential spyware, adware, trojans, keyloggers, bots, worms, and hijackers, in real time. The CyberSecurity landscape has changed. No longer are we protecting against a piece of malicious code – we are defending against persistent adversaries. Find out more about APT’s or Advanced Persistent Threats. (