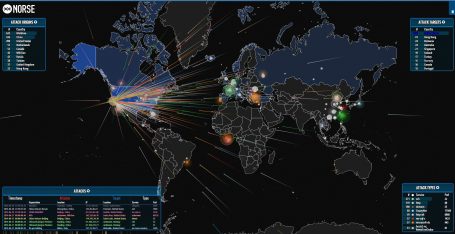
FireEye released the Mandiant® Security Effectiveness Report 2020 which reveals data about how well organizations are protecting themselves against cyber threats and the overall effectiveness of their security infrastructure. The report summarizes the results of thousands of tests performed by experts from the Mandiant Security[…]
Category: Library
Basic rate-limiting middleware for Express. Use to limit repeated requests to public APIs and/or endpoints such as password reset. A brute-force protection middleware for express routes that rate-limits incoming requests, increasing the delay with each request in a fibonacci-like sequence[…]
[pdfviewer width=”600px” height=”849px” beta=”true/false”]https://www.naushad.co.uk/pdf/library/EUR_0616_ezine_19pp.pdf[/pdfviewer]
[pdfviewer width=”600px” height=”849px” beta=”true/false”]https://www.naushad.co.uk/pdf/library/CCISO-Table-of-Contents.pdf[/pdfviewer]
DDoS attacks are making the headlines but if you architect your infrastructure right at the DNS layer, you can significantly reduce or mitigate their impact altogether. Read this whitepaper on building redundancy with a multi DNS strategy. Whether you run[…]
Hackers are hijacking internet routers used in small to large businesses and homes to become a huge Botnet that they can use to launch Distributed Denial of Service (DDoS) attacks against targets from. The attacks were all coming from compromised routers[…]
Features grab banner, detect ssh1 protocol and zlib compression; gather key-exchange, host-key, encryption and message authentication code algorithms; output algorithm information (available since, removed/disabled, unsafe/weak/legacy, etc); analyze SSH version compatibility based on algorithm information; historical information from OpenSSH and Dropbear[…]
A Penetration Testing Framework ______ ______ (_____ \ (____ \ _____) ) ____ ____ ____) ) ___ _ _ | ____/ / _ )| _ \ | __ ( / _ \ ( \ / ) | | ( (/[…]
FastNetMon – A high performance DoS/DDoS load analyser built on top of multiple packet capture engines (NetFlow, IPFIX, sFLOW, SnabbSwitch, netmap, PF_RING, PCAP). What can we do? We can detect hosts in our networks sending or receiving large volumes of[…]
|--Although you should be able to work out who I am, I don't really care, as I can work out who you are. So beware of leaving footprints.--|