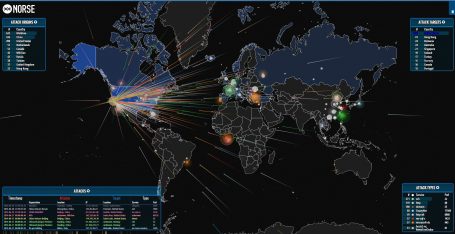
Hackers are hijacking internet routers used in small to large businesses and homes to become a huge Botnet that they can use to launch Distributed Denial of Service (DDoS) attacks against targets from. The attacks were all coming from compromised routers[…]
Category: Blog
What is PCI DSS The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards formed in 2004 by Visa, MasterCard, Discover Financial Services, JCB International and American Express. Governed by the Payment Card Industry Security[…]
The question a wise security manager asks is, can it be done, outside of a James Bond or Mission Impossible scenario? Is it possible to hack a satellite? If you mean use the satellite for your own signals, the answer[…]
Five Questions to Ask When You’ve Been Compromised 1. Which systems and data were affected? 2. How did they do it? 3 . Who did this to us? 4. Is it really over? 5. Can it happen again? Modern security[…]
Anyone who has even the slightest amount of contact with the internet is familiar with the scenario: An email or actual piece of mail arrives from a company who apparently handles some part of your connected life. The letter calmly[…]
Learn How To Find out if Someone is Secretly using your PC: Secure your personal documents being illegally accessed by another person by checking all the logs and details of the activities that had been done on your PC using[…]
Learn How to Send Self-Destructing Emails To Your Friends In Gmail: What if we tell you that you can send a self-destructing email to your friends? That means the sent email will destroy itself after the receiver reads it. This is[…]
Security researchers have discovered a new data-stealing Trojan that makes special use of USB devices in order to spread itself and does not leave any trace of activity on the compromised systems. Dubbed USB Thief ( or Win32/PSW.Stealer.NAI), the malware[…]
If you receive a mail masquerading as a company’s invoice and containing a Microsoft Word file, think twice before clicking on it. Doing so could cripple your system and could lead to a catastrophic destruction. Hackers are believed to be[…]
The sample is in virus total: https://www.virustotal.com/ And it is having low detection ratio due to the native form as Java compiled binary and the key strings used for scanning was encrypted.Open the JAR file with any kind of decompiler[…]
|--Although you should be able to work out who I am, I don't really care, as I can work out who you are. So beware of leaving footprints.--|