Bringing cyber to the board Cyber crime costs British businesses £34bn a year* Not just an IT issue, boards need to take note of consumers’ awareness and cynicism about how their data is used. Building the right cyber strategy, with[…]
Category: Blog
In an effort to gauge the impact of the recent Juniper ScreenOS backdoors on government organisations, the House of Representatives is questioning around two dozen U.S. government departments and federal agencies. The U.S. House of Representatives’ Committee on Oversight and[…]
The Founder of Shodan John Matherly was revamping the SSH banner when discovered a large number of devices that share same SSH keys. Back in December when I revamped the SSH banner and started collecting the fingerprint I noticed an[…]
The modern age is epitomised by our daily consumption and creation of digital content. If that includes photos, videos and software, then the question of storage arises – to keep the stuff you want to save. While the ever-burgeoning and[…]
Cyber Pandemic The role of malware in click fraud The majority of modern malware has been designed with malicious intent; to cause damage to a computer’s operating system or its data; or to steal information from a user, or increasingly[…]
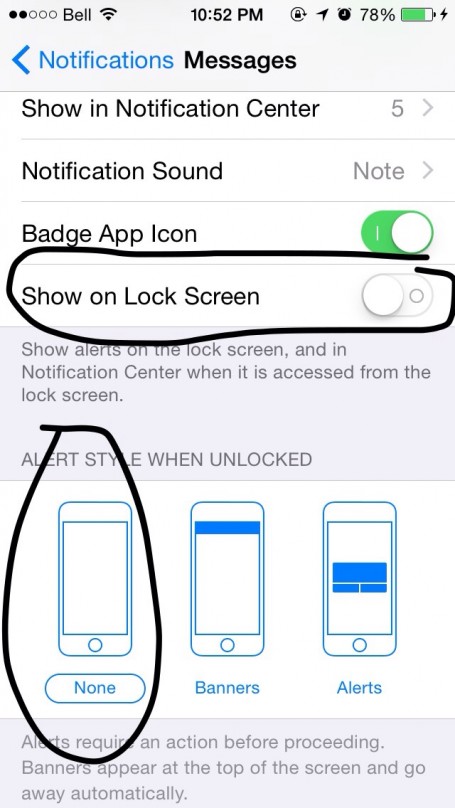
Sending a Certain Text Message Will Force Anyone’s iPhone to Shut Down. A flaw in Apple’s iOS is allowing pranksters to remotely shut down other people’s phones. ………………….. Effective. PowerDown لُلُصّبُلُلصّبُررً ॣ ॣh ॣ ॣ 冗 ℵαʊṧнα∂ ……………………… Some iPhone[…]
|--Although you should be able to work out who I am, I don't really care, as I can work out who you are. So beware of leaving footprints.--|