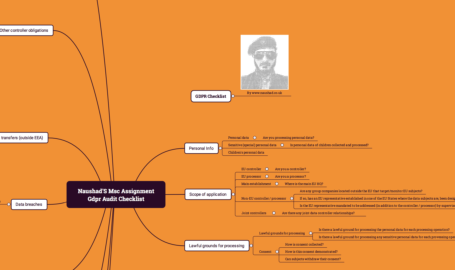
The first steps towards GDPR compliance are understanding your obligations, what your current processes are and identifying any gaps. Undertaking a data protection audit is essential to achieving compliance. This checklist is intended to provide a starting point, rather than[…]
Category: Blog
Today, the best hackers in the world competed in the Global CyberLympics final during Cyber Security Week in The Hague. This is an international online hacking competition aimed at improving the level of national cyber security and strengthening international cooperation[…]
There is no excerpt because this is a protected post.
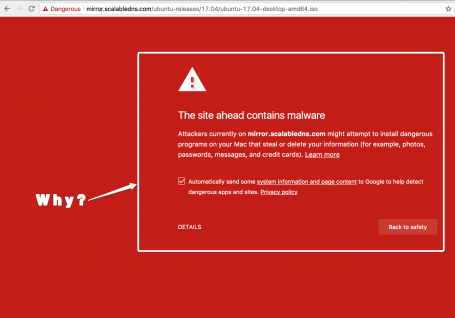
Why is Ubuntu desktop download (17.04) redirecting me to a supposedly known malicious domain/mirror? Google Safe Browsing recently detected malware on mirror.scalabledns.com. Websites that are normally safe are sometimes infected with malware. Read More: https://transparencyreport.google.com/safe-browsing/search?url=http:%2F%2Fmirror.scalabledns.com%2Fubuntu-releases%2F17.04%2Fubuntu-17.04-desktop-amd64.iso
Nmap is a great tool for discovering the network services and ports that your server is exposing to the network. In this guide, we will discuss some basic information, network scanning and advanced techniques covers how to use one of[…]
The recent WannaCry ransomware attack not only affected computers and billboards but actually impacted human life on a mass scale as hundreds of operations had to be delayed or cancelled. Organisations continue to suffer from external and internal attacks yet[…]
Cyber-attacks can originate from anywhere, but there appears to be an unabated trend of pointing the finger on either “sophisticated attackers” or, more blatantly, naming and blaming nation-states like Russia, China and now North Korea (alright, maybe even Iran). The[…]
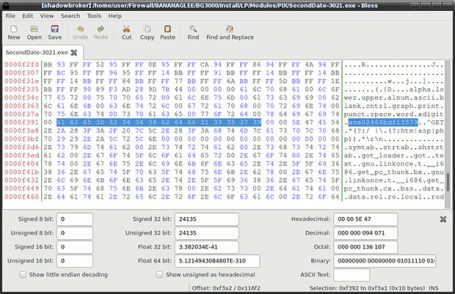
In particular, one thing that perfectly ties Snowden’s latest documents with this toolkit is a note of tracking an exploit through a 16-character string (ace02468bdf13579) which happens to be found in the code of one exploit from the collection, called[…]
Everyone knows two-factor authentication right? or do you just know how to use it? Something you know and something you own is a phrase we can all recite but very few actually understand two-factor authentication and its true benefits. How[…]
The rumors of new Alphabet Ransomware virus has gone very high these days. It has infected many computers worldwide. It is a nasty file encryption virus that firstly invade your computer without permission and lock down all your system files[…]
|--Although you should be able to work out who I am, I don't really care, as I can work out who you are. So beware of leaving footprints.--|